
The Chip Security Act (CSA) is a bipartisan bill that would require high-end AI chips to have the capability to verify their location before being exported. The bill’s introduction comes amid growing evidence that America’s most advanced AI hardware is being diverted to countries such as China, Russia, Iran and North Korea in direct violation of U.S. export controls.
Given AI’s increasingly powerful dual-use applications in military and cyber-offensive domains, the CSA is both an urgently needed reform and one carefully crafted to minimize burdens on U.S. technology companies and chipmakers. With the confidence that sensitive exports are going to their intended foreign buyers, the CSA is essential to enabling the aggressive diffusion of America’s AI technology stack worldwide without inadvertently uplifting foreign adversaries.
Importantly, the Act does not prescribe or endorse any particular method of location verification. Chipmakers would be able to adopt any software-, firmware-, or hardware-enabled chip security mechanism that is technologically feasible and appropriate for verifying a chip’s location following its export or transfer within a foreign country, potentially including direct on-site inspections. A basic reporting requirement would then require companies to notify the Department of Commerce if or when the location of an exported chip changes or is detected somewhere other than the location specified in their license application.
Nvidia H100s advertised for sale on Douyin, China’s version of TikTok
Low-cost, technologically feasible mechanisms for chip geolocation already exist, and have even been in use within commercial contexts for many years. A common software-enabled mechanism involves having the chip send a “ping” to a dozen or more geographically dispersed landmark servers, allowing the chip’s location to be triangulated using the time delay from each server response, given the physics of the speed of light. Despite being relatively low-tech, ping- or delay-based location verification mechanisms are nontrivial to spoof, and have a median accuracy of about 60 miles—precise enough to ensure near perfect country-level accuracy.
Nvidia has acknowledged that its GPUs already have the capacity to transmit and collect the telemetry data needed for location verification, suggesting that geolocation could be implemented through a standard firmware update. This is good news, as it should in principle allow for Nvidia GPUs that have already been exported to be geolocated ex-post. Indeed, a small team of data center security experts recently demonstrated confidential, ping-based geolocation on Nvidia’s flagship H100 GPU using only off-the-shelf, readily available software offerings. As they note, the prototype “was built over a few weeks by a small team of generalist software engineers,” and could no doubt be greatly improved with focused effort.
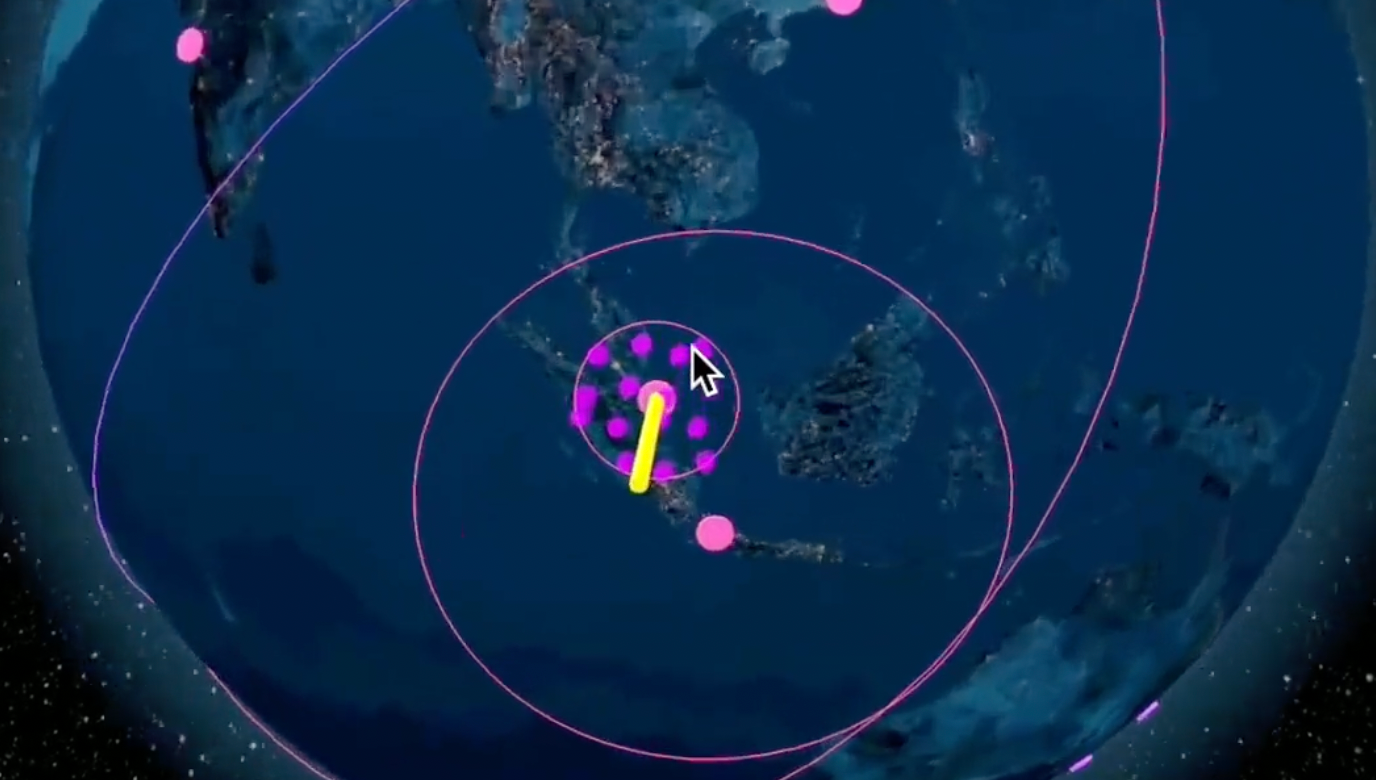
Technical demonstration of ping-based geolocation on an H100 via ping-location.info
To date, Nvidia’s official position has been to not merely minimize the extent of chip smuggling, but to deny that smuggling is occurring altogether. As Nvidia CEO Jensen Huang told reporters in May of this year, “There’s no evidence of any AI chip diversion.” Of course, this is betrayed by the warehouses full of Nvidia GPUs listed for sale on Chinese e-commerce and social media platforms, not to mention the growing number of smuggling operations that have been caught red-handed. Does Nvidia take U.S. policymakers for fools?
Nvidia’s second line of defense is to argue that location verification mechanisms are not full-proof. To be sure, purely software- or firmware-enabled geolocation mechanisms are less robust to spoofing than tamper-proof mechanisms designed into the chip’s hardware, but the latter would likely require significant additional R&D. In the meantime, ping-based mechanisms implemented within existing confidential computing environments represent a powerful, low-cost deterrent to smuggling, particularly for larger data center projects that would require location-spoofing many thousands of chips.
Smuggling operations could be further deterred through the enactment of the Stop Stealing Our Chips Act, another bipartisan bill introduced earlier this year in the Senate. The Act would establish a whistleblower incentive program within the Bureau of Industry and Security, modeled on the Securities and Exchange Commission’s whistleblower program for financial crimes. Individuals who provide anonymous tips about smuggling and other forms of export control violations would be eligible to receive 10 to 30 percent of the collected fines, with exceptions for known terrorists and criminals. Like the CSA, the Stop Stealing Our Chips Act represents a low-cost way to bolster existing export enforcement efforts at scale.
Lastly, opponents of the Chip Security Act may misrepresent the proposal as calling for GPS-tracking, geofencing, or “kill switches” on AI chips, when it does nothing of the kind. Instead, it merely requires makers of export-controlled AI chips to have a reliable means of verifying that their hardware goes to their intended customer. To the extent that key players like Nvidia oppose scalable approaches to export control enforcement, one cannot help but wonder if it’s because they are afraid of what we’ll find.